How to Stop AntiVirus 2009
I’ve often said, even some of the smartest folks I know can find themselves infected with malware. Last week a family member found themselves with frequent pop ups telling them they were infected. They didn’t do anything wrong. Their machine had a vulnerability that allowed the infection just by being connected to the Internet. They finally gave up and downloaded Antivirus 2009. Luckily, they had WinPatrol available to remove it but one simple step could have saved them a lot of anxiety.
It happen to me today as well. I clicked on a legitimate link and suddenly received the following pop up.
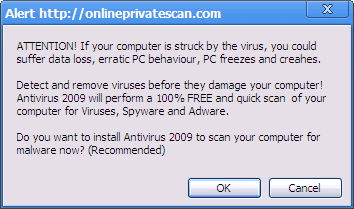
This appeared just by being on the Internet
It won’t do you any good to click any button including the X. The result will always be a fake scan by Extortion-ware Anti Virus 2009
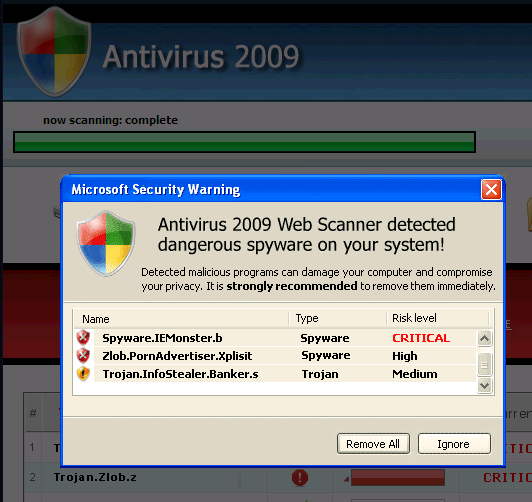
STOP here, clicking on the Red X won't save you.
Eventually, most folks give up and end up downloading Antivirus 2009 which turns into Extortion-Ware. They try to convince you that upgrading and paying is the only way to clean up the viruses listed above.
Solution: Ctrl-Alt-Del
The answer to this situation is simple. As soon as you experience your first pop up that can’t be closed by the X in the upper right-hand corner your next step should be Ctrl-Alt-Del. This is your opportunity to open the Windows Task Manager. Check the list of Applications and Kill your browser.
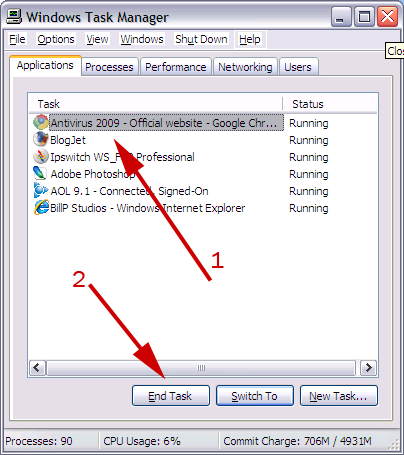
Windows XP Task Manager
You could also use WinPatrol’s Active Task list to kill the browser but since you only need to kill a single task, Ctrl-Alt-Del is even easier. If however you did download AntiVirus 2009 you’ll want WinPatrol so you can sort, select and kill multiple tasks in a single operation. You can also use WinPatrol to “Delete File on Reboot” any files which don’t seem to want to go away. WinPatrol users see http://www.winpatrol.com/helpme.html.
Prevention: Security Updates
Your next step is to make sure you’ve downloaded all the available Windows security updates. Many of you know, I typically recommend against automatically installing new Windows updates on the day they’re released. Last month Microsoft did release a number of new security patches. Guess what? It’s time to update.
Let me repeat. The first pop up I received came with I clicked on a valid link. I went back to the same link and it was fine. IT’S TIME TO UPDATE!!!
Labels: Antivirus 2009, remove, WinPatrol
 Bits from Bill
Bits from Bill


18 Comments:
This time you beat me to the punch!
In the "Tip of the Day" series I am doing for NCSAM, a Freedomlist member suggested Ctrl + Alt + Del to close popups. The post is scheduled to be published tomorrow so I have added a link to your "real-life example".
I just engage the firewall's lock "engage internet lock" then close the browser. Before I turn the browser back on or open the firewall internet connection I run the following: (note: not an endorsement of this software, just what I run to clean up my system everyday).
Evidence Eliminator (my license was paid for long before spammers got a hold of this product).
PurgeIE
PurgeFox
CCleaner
EasyCleaner
Then I go a quick registry sweep for the referenced popup item.
George
From the description, it sounds like this was just basic javascript alert boxes and redirects. In that case, the worst thing they can do to is to spam you and try to socially engineer you, unless your browser is broken, in which case you have bigger problems.
Some popup spam rises to the level of a denial-of-service attack on the browser (it sounds like this one does), in which case the ctl-alt-delete tip is useful. Personally, after clicking X on the popup, I'd add the step of trying to close the current browser tab before I resorted to killing the whole browser.
I wouldn't be too alarmed by this if it is infrequent, as there are other more probable explanations than a existing infection on your PC.
In any case do make sure you are fully patched and run some scans for malware. That's one thing I can agree with completely.
From the description, it sounds like this was just basic javascript alert boxes and redirects. In that case, the worst thing they can do to is to spam you and try to socially engineer you, unless your browser is broken, in which case you have bigger problems.
Some popup spam rises to the level of a denial-of-service attack on the browser (it sounds like this one does), in which case the ctl-alt-delete tip is useful. Personally, after clicking X on the popup, I'd add the step of trying to close the current browser tab before I resorted to killing the whole browser.
I wouldn't be too alarmed by this if it is infrequent, as there are other more probable explanations than a existing infection on your PC.
In any case do make sure you are fully patched and run some scans for malware. That's one thing I can agree with completely.
Good advice as always Bill.
Unfortunately the warnigs this delightful threat throws up are worrying and plausible to inexperienced users (the same users who "don't need" Scotty's protection). When a machine has been successfully infected users will see fake bluescreens, fake shutdown messages, changed screen resolutions - the lot. Several of our clients (I run an IT support company) have panicked and been infected this way. Fortunately the problem can be resolved swiftly and effectively by malwarebytes.org's anti-malware. (I have no connection with them - just keen to save time and frustration!)
Hi Bill, per usual your warnings are prompt, relevant and timely but unfortunately on a few occassions just a tad late for me. However, most appreciated if for no other reason they help my own understanding of how (to some extent that is) these things have happened.
I am in Australia and my very recent experience was similar to yours in that late last week I had a pop-up appear (despite having pop-ups disabled in my IE7 browser. Which appeared to me to be a legitimate Windows Message, suggesting that I should install a download called "AntiSpywarePro". I was smart enough to take the "cancel" option rather than to take the "ok" to download. However the message was persistent and wouldn't go away, per your experience even when trying to close the message by taking the "X" to cancel.
Unlike you however, I had already downloaded the latest Windows Updates but they seemingly had or did not stop all of this happening. However, I was on this occassion fortunate that I also have "Microsoft Windows Live OneCare" installed as my AntiVirus program and after trying several times to close the Windows Message box LiveCare stepped in to rescue me by telling me that I had downloaded (which I hadn't knowingly done) a Trojan named something different to the name I had been presented with and it suggested I might like to perform a scan to remove it. Which I did, rebooted and all seemed fine...
The sequel to this occured a few days later my scheduled weekly AOL system scan ran and told me that I had "Windows Messenger" running despite it anticipating the Windows default setting as being "Off", which it then prompted me to "fix" this which I did. So to all intents I am now back to being safe again at least fttb. Though I have no idea what caused the Windows Messenger to be switched "on".
I am not a technical expert but am hoping that this extension to your Comments will help you and others to better understand what may have caused this to happen and how I 'seemingly' managed to avert the same or similar experience to your own.
Keep up the great work Bill and Congratulations on your recent well deserved MVP award.
Just this week I was reinstalling Window on a hopelessly infested Dell 2350 amd I had no sooner completed the install than a Windows Messenger box popped up say that there had been an error made while creating the registry. I recognized the scam and used the Alt-CTRL+Delete route to shut it down and then checked services and found Messenger disabled but running. I uninstalled the Messenger and have had no problems since. The Windows reinstall was done with a Dell recovery disk. Some of those messages must be loaded at the manufacturer, somehow.
My question is, how to stop Antivirus 2009 once a customer has gotten really infected. (without doing an erase & reload (E&R))
1. The Task Manager will not open.
2. You cannot access "My Computer" or any other Folder, file or program.
3) "IF" you can bring the system up in Safe Mode, it doesn't do you much good because "IF" you can get System Restore started, there are either no restore points or only one restore point and you REALLY don't want to use that one.
4. It actively attacks Sysinternals Process Explorer and will not allow Root Kit Revealer to run.
So far, I'm batting about .500 against it, and the times that I won, I'm not really sure what exactly did the trick. The Most effective and crippling to the Virus is removing the drive, installing in another system as a slave and scanning. Then you mainly have to worry about browse redirects that can get you re-infected quicker than you can physically react.
What is more interesting is that Yesterday, 10/09/08, I faced off with Antivirus 2010 and actually won, I hope. The next day or two will tell. "War is Hell"
I got hit last Sunday with no less than eight virus,trojans, etc. all at once it seemed. Mcafee ignored the problem. PC Pitstop would find, but not kill them. Antivirus 2009 was the lesser of the problems. Finally, I picked the best knowledge from some virus forums (just go to a search engine an type in your favorite virus) and got free copies of Advast and Super-antispyware. 15 hours later I was clean.
Spybot-S&D found it killed it and left my pc free from all trace of av 2009 so it gets my vote
andy
Hello again Bill,
Looks like the same "You are infected" scam hit everyone this week. I operate Netrepreneurs.us and consider myself not quite a guru but very experienced with the Internet an dcomputers since 1989 when I started selling cars over the Internet. I sold my dealership in 94 because I was selling far more cars on the Internet than from the lot.
The same "you are infected" pop up hit me, too. I was stupid enough to hit the X to kill it. It immediately downloaded on my computer. With in several minutes, I was experiencing an unbelievealbe slow down. I went to one of my other computers and walla...all four computers I have on my home network were infected and slower than waiting for Christman. I did a little searching and came up with www.bleepingcomputer.com who had detailed instructions on what this scam (virus or trojan) actually is and how to remove it. I have been working since last night with 4 hours of sleep and all day today and am still working on it. I also came up with the malwarebytes.org's anti-malware but that didn't do it for me. I also came across this site in a further attempt to figure out how to get rid of it and get my super fast computers back!!!!!!
Now I am following the suggestion of one of your repliers and going to try Spybot S&D and Super-antispyware in hopes that will bring my little babies' swiftness back to me.
Keep up the good work,
webmaster@Netrepreneurs.us
I suggest everyone spend a few minutes every day reading blog.trendmicro.com and malwaredatabase.net/blog to stay up on current threats.
System restore, if in service, will have the infection. Turn off system restore, then remove the infection, reboot, and do anther virus check before activating system restore.
Jim
Okay for annonymous and the others that got that virus, or trojan that causes you issues, you might want to get the full malware bytes Anti-Malware Toolkit, it has everything you need to find and fix the issues, also get the Windows Defender from microsoft as well. I contend with these viri and trojans on a regular basis with my friends and neighbors, who all have come to me and pay me to remove those problems from their hd's I also use Ad-Aware 2008 from Lavasoft as well. Google for the Anti-Malware Toolkit and get it, and use it with the instructions I am posting here and you should be able to remove any of these problems once and for all. I will tell you it will take a few hours to do, to run everything as instructed, but when you are done, your systems will be clean. When you get the Anti-Malware Toolkit and any other program, make sure they are updated, also you may want to install Avast or AVG antivirus programs on your computers as well, they work way better than Norton's and McAffee, and are free. Here are the instructions for the Anti-Malware Toolkit. Also you may want to boot in safe mode with networking, sometimes you may forget to update the programs, and you can update them on the fly this way, before using them
This process has been found to be the very best in eliminating and terminating infections. This process will also help to prevent infections from spreading as the infections are removed. You will also want to update each programs definitions/database if updates are available.
Install SpywareBlaster.
Install CCleaner.
Install RogueRemover Free.
Install SUPERAntiSpyware.
Install Malwarebytes Anti-Malware.
Install Spybot S&D.
Order of Operations
By following the directions listed below, you increase your chances for a fast reply on getting your HijackThis log and your computer cleaned.
Please follow these directions:
Order of Operations:
Boot your computer into Safe Mode by pressing F8 before the Windows logo screen on bootup.
Run SpywareBlaster.
Run CCleaner.
Scan for viruses with the Recommended Software and Online Virus Scanners.
Run RogueRemover Free.
Run SUPERAntiSpyware.
Run Malwarebytes Anti-Malware.
Run Spybot S&D.
At this point you should reboot your computer and run HijackThis to post a log on our forums.
Run HijackThis.
Run Windows Update.
Unable to run Windows Update? Fix most common errors with DjLizard's Dial-a-fix!
Cleaning & Settings
This section will describe how to update the recommended applications and allow you to configure each program with the best settings for malware removal.
SpywareBlaster
SpywareBlaster doesn't scan and clean for spyware - it prevents it from ever being installed. It will also stop malware from communicating with its host server. This helps to stop popups and malware from functioning and further spreading the infections.
Update Instructions:
Under "Quick Tasks" click "Download Latest Protection Updates".
Click the "Check for Updates" button.
Activation:
After updating, click "Protection" near the top.
Under "Quick Tasks" click "Enable All Protection" and you're finished with SpywareBlaster.
Need further assistance? Refer to the SpywareBlaster screenshots.
CCleaner
CCleaner helps to clean more than just junk files in your computer. It can also help to clean out and remove malware from your %TEMP% folders and other common temporary directories where malware can reside.
Scan Settings:
Select the "Windows" tab and check every option.
Select the "Applications" tab and check every option.
Click the "Run Cleaner" button.
The following items should not be checked.
"Memory Dumps"
"Windows Log Files"
"Old Prefetch Data"
"Hotfix Uninstallers"
Explaination:
The Memory Dumps cleaning option will remove any memory dumps that are generated when a program crashes on your computer. Many technicians can use these memory dumps to tell you exactly what caused the crash. These memory dumps are also sent to a crash analysis center at Microsoft when you use the Error Reporting feature. Reporting these errors and sending the crash dumps help all users because hotfixes are often issued to fix the very problem that made the program crash.
The Windows Log Files cleaning option will also remove another memory dump file called user.dmp that is generally placed in %ALLUSERSPROFILE%\Application Data\Microsoft\Dr Watson\. This is also useful for technicians to help diagnose errors that cause programs to crash, similar to the Memory Dumps above. In addition, this cleaning option will also remove log files from both program installations and Windows Updates. A user or technician can refer to these generated logs to determine the source of the installation problem if a problem occurs.
The Old Prefetch Data cleaning option will decrease your system performance. The impact that cleaning/deleting the prefetch data has on your system is well documented by technicians and Microsoft staff. Prefetch is designed to allow your applications to load faster.
The Hotfix Uninstallers cleaning option will remove every hotfix uninstaller. This is a bad option for CCleaner to have. If you have this option checked and you remove your hotfix uninstallers, should you ever have an issue with an update (hotfix) from Microsoft, you would not be able to uninstall the problematic hotfix. This could potentially result in your system being crippled.
Making certain the above options are not checked will ensure your computer remains in proper working order and have better performance.
Note: The first run can take several minutes. You may wish to uncheck some options if CCleaner takes longer than five minutes.
Advanced users only:
This section deals with changes to your computer's registry. If you do not feel comfortable making changes to your registry then skip this section. It is recommended that you create a folder named "Backups" in your CCleaner folder inside the Program Files directory and save your registry backups there.
Click the "Issues" button and check every option.
Click the "Scan For Issues" button.
Click the "Fix selected issues..." button.
Click "Yes" when asked to backup changes to the registry.
Save the backup for repairing these issues so you may find it easily when you need it in the future.
Need further assistance? Refer to the CCleaner screenshots.
RogueRemover Free
RogueRemover is an excellent freeware scanning utility that quickly and efficiently scans your computer for known malicious rogue software.
Update Instructions:
Click "Check for updates" in the main program window. A new window will appear.
Click "Check for updates".
If any new updates are found, click "Download".
After updating, click "Close" to return to the main program window.
Scanning:
Click "Scan".
Remove any malicious items found.
Need further assistance? Refer to the RogueRemover screenshots.
SUPERAntiSpyware
SUPERAntiSpyware Free Edition is a free program that helps protect your computer against pop-ups, slow performance, and security threats caused by spyware and other unwanted software.
Update Instructions:
First Install:
Click "Yes" on the message box that appears asking about updating.
Regular Use:
Click the "Check for Updates..." button.
First Run:
A Setup Wizard will appear to assist you.
Click "Next"
Do not enter any email address and then click "Next".
Uncheck Automatic Update checking (only available in paid version) and then click "Next"
Uncheck "Send a diagnostic report to our research center"
Protect Homepage appears, click "Do NOT Protect".
Scan Settings:
Click the "Preferences" button.
Under "General and Startup" uncheck the following:
"Start SUPERAntiSpyware when Windows Starts"
"Show SUPERAntiSpyware icon in system tray"
"Show splash screen on startup"
Under "Scanning Control" uncheck the following:
"Ignore files larger than 4MB"
"Ignore non-executable files"
"Display scan option in Explorer context (right-click) menu"
Under "Scanning Control" check the following:
Apply a check to "Terminate memory threats before quarantining"
You can now click "Close" for the Preferences as all settings have been set accordingly.
On Exit
Click "Do not show this message next time" if it appears.
Need further assistance? Refer to the SUPERAntiSpyware screenshots.
Malwarebytes Anti-Malware
Malwarebytes Anti-Malware is a free program that will scan your computer for numerous infections, including Vundo, SmitFraud and other dangerous malware.
Update Instructions:
Click on the "Update" tab.
Select "Malwarebytes.org" in the "Update mirror" dropdown box.
Click "Check for Updates".
Scan Settings:
Select "Perform full scan".
Click "Scan" to begin scanning.
Need further assistance? Refer to the Malwarebytes Anti-Malware screenshots.
Spybot S&D
Spybot S&D searches your hard drive for so-called spy- or adbots; that is, little modules that are responsible for the ads many programs display. Many of these modules also transmit information, including your surfing behavior on the Internet. If it finds such modules, it can remove them. In most cases the host still runs fine after removing the spyware/adware.
Note: You do not need to run or activate TeaTimer. If you wish to have the extra protection you should use Windows Defender's Real Time Protection.
First time only:
Click "Mode" -> "Advanced".
Click "Yes" on the message box that appears.
Click "Settings" -> "File Sets" -> Make sure everything is checked.
Update Instructions:
You can run spybotsd_includes.exe or follow the directions below to update Spybot S&D.
Click on the "Update" button.
Select all updates.
Select a server to download updates from. It is recommended that you use one close to where you live.
Click "Download Updates".
Scan Settings:
Click "Immunize" and allow it to scan, then click "Apply".
Click "Search & Destroy" and then click "Check for Problems".
This will find any malware installed and also offer to clean your usage tracks (MRUs).
If you have your folders set in a special way then do not check Windows Explorer in the usage tracks reported.
Need further assistance? Refer to the Spybot S&D screenshots.
HijackThis
HijackThis is a free utility which quickly scans your Windows computer to find settings that may have been changed by spyware, malware or other unwanted programs. HijackThis creates a report, or log file, with the results of the scan.
Scan Settings:
Uncheck "Show this frame when I start HijackThis" at the bottom.
Click the "Scan" button.
Click the "Save log" button.
Name your log with your user name.
Example: If your username is User123, then you would save your log as User123-Hijack
Need further assistance? Refer to the HijackThis screenshot.
Conclusion
Haven't registered yet for the Lunarsoft website and forums? Then please register with us!
If you have registered with Lunarsoft already, please post your log on the HijackThis Logs forum.
After your computer has been given a clean bill of health, you should read the PC Security page for adding extra protection to your computer.
Good luck, Tarun - Lunarsoft
Retrieved from "http://wiki.lunarsoft.net/wiki/PC_Cleanup"
7:38 PM
i have found my favorite way to stop this from taking over... run superantispyware from superantispyware.com or majorgeeks.com and let it remove all objects, then run malwarebytes.org's anti spyware program... has kept me from reinstalling!
I have cleaned two machines of this stuff after it was installed. I had a client (small office, June 08) who actually followed the instructions and downloaded and installed the 2008 version of this malware, then paid the 49.95 online for the 'full version'. Needless to say, the charge was to a business in the Republic of Moldova. The installed version was quite intertwined with the OS (winxp sp2) and included the Russinovich 'joke screensavers' which were called when we tried to install Symantec AV (McAffee was already installed and completely overwhelmed). When the Symantec installation was under way, the screensaver was triggered in full screen demo mode, perfectly imitating a BSOD. Many people will cycle the power at this point, but all you need to do is press the escape key. After running Spyware S&D and a Norton AV scan, it looked like everything was removed. A visual scan of the the temp and cache folders turned up two small apps in the java temp folder which I deleted manually.
Hi, I have had the latest incarnation of Anti-Virus 2010 on a couple of friends machines and another called Internet Security 2010 on a business machine recently, in all cases I had to rebuild them, once the malware takes hold it initially flashes up the screens as above but then it has the effect of logging you off imeadiatly after logging on, even if you try to start in Safe Mode it will still stop you from running CMD, Regedit, etc. I spent around 3 hours trying to remove it but eventually gave up. I would quite happily donate £5 to a fund to have to low life that wrote this sort of stuff taken out of the gene pool!
Steve
I have an irritating and ridiculous antivirus 2009 thing on my computer. How do I get rid of it?
Post a Comment
<< Home