April Security News is Serious
Many of my friends have been asking for my opinion of a couple security issues which have been in the news.
The first is Windows XP which was launched in September of 2001. Microsoft announced last year that after April 8th, 2014 it would no longer provide support for Windows XP and Office 2003.
The second concern is for something known as HeartBleed. This could be dangerous to anyone who visits a website no matter what kind of device you use.
Microsoft Windows XP
I realize that many of you can not or will not upgrade your computer currently running Windows XP. It may not happen today or even next month but it’s only a matter of time before your computer is infiltrated and is useless. Start putting aside some money, backup your data regularly and look for alternates to programs you can’t do without. I’m sorry but it’s only a matter of time.
If someone on your home or business network is using Windows XP, turn off their access. When their machine is attacked it will compromise your entire network. ![mifihotspot[8] mifihotspot[8]](http://lh4.ggpht.com/-P2R9WaFc3nc/U0Ydk3C6WCI/AAAAAAAAAqc/tqZ762CQ4J0/mifihotspot%25255B8%25255D_thumb%25255B5%25255D.jpg?imgmax=800)
If they really need Internet access consider getting them a separate connection perhaps through their phone or with a separate hotspot.
Many of you asked about using WinPatrol which is a great idea but doesn’t address the big picture. The security guru’s at Microsoft spend a lot of attention on flaws or vulnerabilities in software. When they find a hole that lets hackers in, they create a patch. After a great deal of testing they release fixes on what we called “Patch Tuesday."
WinPatrol will continue to notify you of regular changes to your computer but the ability to patch vulnerabilities isn’t its specialty. What I will be doing is paying attention to what I hear from hackers. When possible, we will notify WinPatrol users if a particular file or ActiveX component is found to have a vulnerability. WinPatrol PLUS will allow you to disable ActiveX components by setting their Kill Bit. This is the most we can do and will require quick action.
OpenSSL - Heartbleed
On Monday researchers disclosed a serious flaw in a open source program used by almost half the web servers around the globe. A version of the program called OpenSSL allowed hackers to grab a chuck of recently active protected memory. This memory could contain anything from names and passwords to someone’s grocery list to decoded government or industrial secrets. Any kind of data that is communicated could be snatched. After collecting unlimited chucks of data a hacker could make a game out of figuring out what segments could be valuable. Each chunk was 64K like the total addressable memory of the Commodore 64.
Some media outlets like the BBC have repeated the advise to change every password you have. There is no trustworthy list of up-to-date/time safe computers but a list created yesterday claims to have tested 10,000 popular sites. Most have been updated by now but you’ll want to be sure before changing any password or even signing on. An updated list should be available soon.
A number of tools for consumers have sprang up allowing you to verify in real-time if a website is currently safe. I found the following to run my own tests.
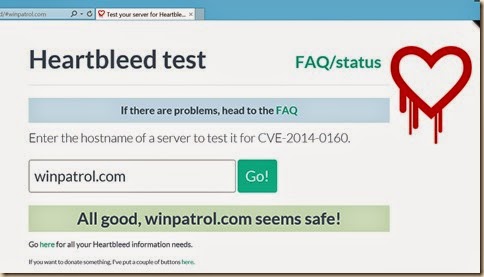
Click image to test your favorite site
My web sites have been hosted by the company, Verio and I was pleased to see my information was safe It doesn’t mean it was always safe but if not, at least Verio was quick to apply a fix. I can confirm no personal or financial customer data is stored on our web servers.
I wouldn’t necessarily advise you to change all your passwords. Before you do, you’ll certainly want to be sure the company is aware of Heartbleed and has updated their security. Over 56.8% of the companies on the list of 10,000 are listed as safe because they don’t even use OpenSSL. Another 36.9% tested safe yesterday. That leaves only 6.3% were vulnerable when the news was announced.
I have changed some of my more important passwords but I regularly changes passwords anyway. I did change my Yahoo passwords since they were mentioned in many news reports and acknowledged using OpenSSL. Considering Google was involved in disclosing this bug it’s interesting that Yahoo was used as an example. Many friends of Google were notified so they could update their version of OpenSSL before the information was made public.
While you may notice my tone is not meant to create panic, I personally consider this failure as devastating. I started developing online services for consumers 30+ years ago and this is the “utmost cock-up”. I don’t fear the damage caused by this threat as much as I worry about what this general lack of oversight represents.
You can find more details online from our favorite security investigator, Brian KrebsonSecurity and official reports sponsored by Homeland Security on the Carnegie Mellon CERT database. The list of 10,000 is located at
https://github.com/musalbas/heartbleed-masstest/blob/master/top10000.txt
Labels: Github, Google, HeartBleed, Krebs, Open Source, OpenSSL, Security, Windows XP, WinPatrol, Yahoo
 Bits from Bill
Bits from Bill


0 Comments:
Post a Comment
<< Home