Biggest Security Hole Continues to be People
In the old days the easiest way to access a computer system was to go directly through a human. It wasn’t always done through the use of wargames dialer which dialed up phone numbers in search of computers with modems. Most time it was as easy as calling a secretary at the computer center and saying…
“Hi, this is Fred from IBM. We found a problem with the computer system and it appears most of your data has disappeared. I’m not sure if you’re responsible but we need your account and password to fix this problem.”
It may sound silly but it worked and the same methods are used today. They’re just a little more sophisticated.
When the storm Trojan was first detected I didn’t give it a lot of consideration. I even suggested that everyone was over reacting.
“Are attachments like this still getting through Email filters? Are people downloading attachments with names like, video.exe, full video.exe, Read More.exe, Full Text.exe or Full Clip.exe to see new stories? I say no. At least not to the extent deserving of this weekends attention.”
I’m willing to admit my evaluation at the time may have been shortsighted. When the attack is this large, it doesn’t take a huge percentage of victims for a problem to become serious.
It’s not as difficult as you might think to get folks to fall prey to a socially engineered attack. I’m sure a large number of intelligent people believed it when “Your family member has sent you an eCard” arrived in their Email.
The most effective attacks I’ve been tracing try to scare readers into taking an action when they think they’ve already had their account or machine compromised.
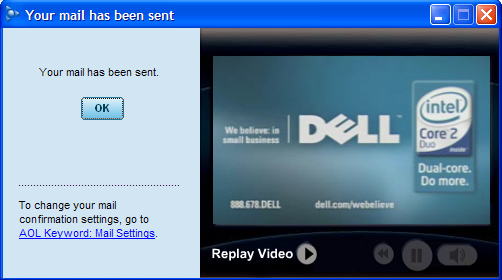
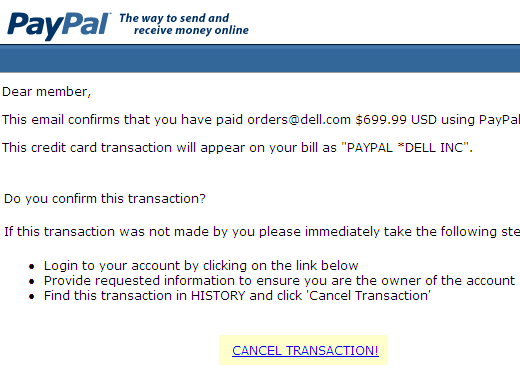
The following are other examples I’ve seen regularly in my Email. What would you do if you thought someone had purchased a new Dell computer using your PayPal account?
And how bad would you feel if someone gave you a bad recommendation on eBay?
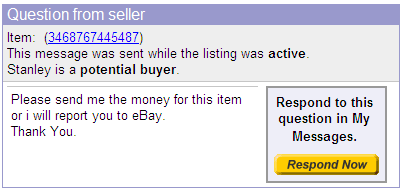
I have a pretty good imagination and it didn’t take me long to think of other examples on my own. Here’s one that targets users in the U.S and I’m guessing it would trick a number of folks into granting full access even pass their firewall.
Obviously, user education will never be 100% effective but don’t panic. A lot of folks like myself will continue to spend time coming up with new ideas on how to reduce and/or prevent damages.
In case you are interested, you really can receive Amber alerts on your computer or mobile device by signing up at http://www.amberalert.gov/
Labels: amber alert, phishing, SPAM, storm, tricks
 Bits from Bill
Bits from Bill